Cyber Security Services
- Home
- Cyber Security Services
Cyber Security Services
- 24/7 Monitoring
- Wireless Networks
- Network Security
- Firewalls
- IDS/IPS
- Endpoint Security (Computer Hardening)
- Disaster Recovery and Response
- Compliance Auditing
- Ransomware and Malware Protection and Response



24/7 Monitoring “Peace of Mind”
- A company’s network is a vital part of its core business operations. Therefore it requires 24/7 monitoring to ensure that malicious activities are detected, reported and remediated.
- Using the latest Cyber Security tools, we are able to continuously monitor activities on your network to respond to threats using Automated response techniques.


Wireless Networks
- Wireless Networks can be points of weakness for any company. Having strong Wireless security is vital to protecting your business.
- Configure your wireless network to meet the business needs.


Network Security
- There is no all in one solution when it comes to Cyber security. Network security works as another layer of protection to ensure your critical devices are protected.
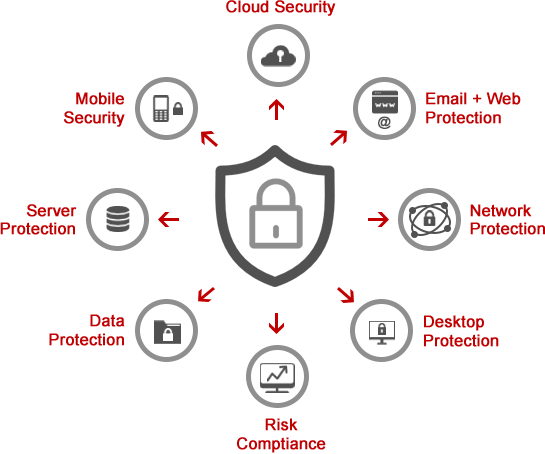

Endpoint Security
- Improving the security on all the devices connected to your network is crucial in protecting your business.
- Just one device being infected can put the entire network in jeopardy.
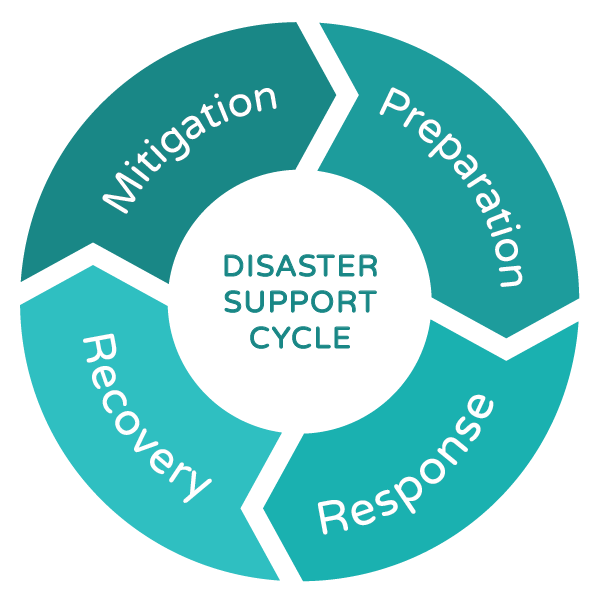

Disaster Recovery and Response
- Back ups allow for a business to safeguard their data in the event of a disaster.
- They can cut the time it takes your business to recover.


Compliance Auditing
- Different industries require compliance in different shapes and forms.
- With our tools it becomes simpler to automate compliance reports for your organization.


Ransomware and Malware Protection and Response
- Your network is always in danger of falling victim to a computer virus.
- Ransomware attacks have been increasing exponentially in the last two years and are more common to affect SMB’s who are more vulnerable.
+
Satisfied Clients
+
projects done
+
team advisors
+

